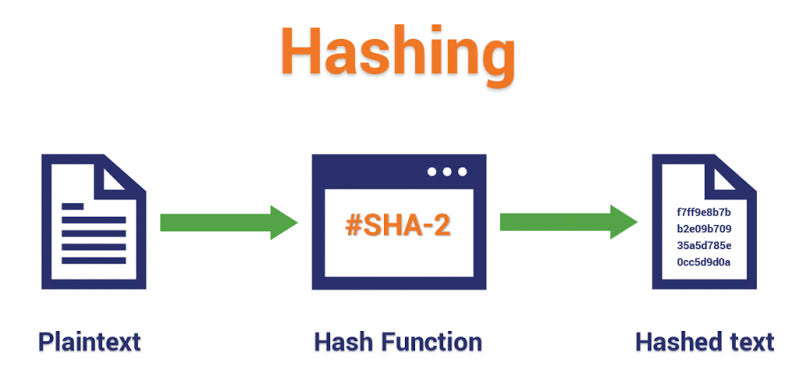
Depending on the utilisation of hashing algorithm is considered to be a very good idea on the behalf of organisations to ensure that everybody will be perfectly able to work in the remote systems with multiple files being shared and dealing with several other kinds of login attempts becomes easy. In this particular case, different kinds of activities will be easily carried out by the organisations to ensure that there will be no chance of any kind of chaos and everyone will be on the right track in dealing with the things. Hashing algorithms are considered to be the fundamental part of cryptography that is perfectly referring to the concept of chopping the data into smaller and big pieces and ultimately it makes it very much difficult for the end-user to go back to the original text or state. This particular function is known as the comprehensive type of algorithm that will generate the fixed-length result or has a value from a specific input data and further makes sure that encryption will be perfectly carried out that will be converting the plain text to the encrypted text very successfully. This concept will further help in making sure that everything will become very much difficult for the hackers to make a lot of sense and the protection element will be given a great boost. In this particular case whenever the organisations have to ensure the password security then hashing is the only thing that will be ensuring that the password will be carried out very easily and there will be a very comprehensive level of storage into the peers so that the user name in the database table will be dealt with very easily without any kind of doubt. Hashtags can be perfectly used in this particular case for password storage, integrity check, digital signature and several other kinds of related things so that overall goals are very easily achieved without any kind of doubt.
What are the most ideal cryptographic hashing functions?
There are some of the most important aspects to be taken into consideration by people at the time of dealing with the hashing functions in this particular case and some of the most common ones have been explained as follows:
- Should behave as a one-way function: The organisations cannot go back to the original text once it has been subject to the hashing algorithm which is the main reason that getting a specific result in this particular case is directly associated with having a clear idea about the initial inputs so that overall goals are very easily achieved and there is no chance of any kind of chaos.
- Hashing functions in this particular case should use the avalanche effect: Another very important thing which the organisations need to take into consideration in this particular case is to be clear about the utilisation of the input that will help in providing people with particular output and for any kind of minor change in the input there will be a drastic change in the output. Hence, is very much clear about the utilisation of the avalanche effect, in this case, is important to avoid any kind of chaos.
- Faster in terms of computing: For any kind of input data subjected to be hashing algorithm it is very much important for people to get the results within seconds so that there is no chance of any kind of problem and everything will be built very strongly without any kind of doubt.
- The output should not have any kind of collision: The output of two input parameters should never be the same because we look at the length of the hashing function output is important so that everybody will be able to have a clear idea about the technicalities in this particular case without any kind of problem.
- Hashing functions are deterministic: The output of one input parameter in this particular case has to be the same irrespective of the concept whatever people are thinking and how many times people are using it. This particular concept will be especially coming in handy whenever multiple people will be using the things to be verified at different points of time without any kind of doubt in the whole process.
Read Also: How Modern ERP For Manufacturing Can Boom Your Business?
It is very much important for people to be clear about the basic technicalities in this particular world so that everyone will be able to bring the hashing algorithm into action without any kind of doubt. Whenever the organisations will be speaking about the concept of passwords and credentials in the beginning then there will be no need to worry because the understanding of this particular system is very much important so that the rating of the checksum will be carried out very easily and everybody will be on the right track of dealing with the generation of a specific five. In this particular case, everybody will be on the right track of dealing with the correct recipient so that overall goals are very easily achieved in there will be no chance of any kind of issue. In this case, everybody will be able to deal with things in a very well planned manner so that overall systems are perfectly made available without any kind of skills.
Having a clear idea about different types of the hashing algorithm is available in the industry in the form of MD or message digest, secure hashing algorithm family, Whirlpool, RIPEMD and several other kinds of related things are important to avoid any kind of technical issues at any step throughout the process.
Even though different kinds of versions are perfectly introduced in the market with the help of this concept everyone will be able to deal with things with the latest technological advancements without any kind of doubt so that business continuity will be easily achieved and everybody will be able to enjoy the perfect implementation of different kinds of credentials very successfully. Hence, depending on companies like Appsealing, in this case, is a very good idea so that everyone will be on the right track of dealing with the things without any kind of hassle.